NoaBot: Latest Mirai-Based Botnet Targeting SSH Servers for Crypto Mining
A new Mirai-based botnet called NoaBot is being used by threat actors as part of a crypto mining campaign since the beginning of 2023.
“The capabilities of the new botnet, NoaBot, include a wormable self-spreader and an SSH key backdoor to download and execute additional binaries or spread itself to new victims,” Akamai security researcher Stiv Kupchik said in a report shared with The Hacker News.
Mirai, which had its source code leaked in 2016, has been the progenitor of a number of botnets, the most recent being InfectedSlurs, which is capable of mounting distributed denial-of-service (DDoS) attacks.
There are indications that NoaBot could be linked to another botnet campaign involving a Rust-based malware family known as P2PInfect, which recently received an update to target routers and IoT devices.

This is based on the fact that threat actors have also experimented with dropping P2PInfect in place of NoaBot in recent attacks targeting SSH servers, indicating likely attempts to pivot to custom malware.
Despite NaoBot’s Mirai foundations, its spreader module leverages an SSH scanner to search for servers susceptible to dictionary attack in order to brute-force them and add an SSH public key in the .ssh/authorized_keys file for remote access. Optionally, it can also download and execute additional binaries post successful exploitation or propagate itself to new victims.
“NoaBot is compiled with uClibc, which seems to change how antivirus engines detect the malware,” Kupchik noted. “While other Mirai variants are usually detected with a Mirai signature, NoaBot’s antivirus signatures are of an SSH scanner or a generic trojan.”
Besides incorporating obfuscation tactics to render analysis challenging, the attack chain ultimately results in the deployment of a modified version of the XMRig coin miner.
What makes the new variant a cut above other similar Mirai botnet-based campaigns is that it does not contain any information about the mining pool or the wallet address, thereby making it impossible to assess the profitability of the illicit cryptocurrency mining scheme.
“The miner obfuscates its configuration and also uses a custom mining pool to avoid exposing the wallet address used by the miner,” Kupchik said, highlighting some level of preparedness of the threat actors.
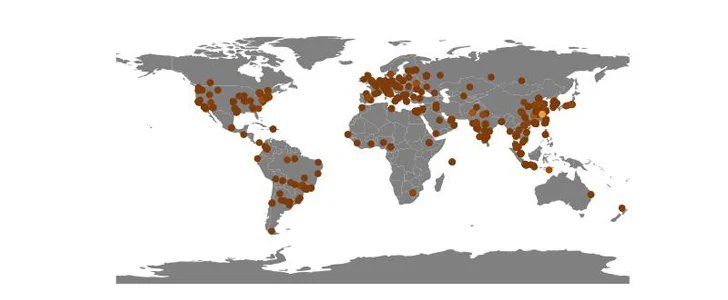
Akamai said it identified 849 victim IP addresses to date that are spread geographically across the world, with high concentrations reported in China, so much so that it amounts to almost 10% of all attacks against its honeypots in 2023.
“The malware’s method of lateral movement is via plain old SSH credentials dictionary attacks,” Kupchik said. “Restricting arbitrary internet SSH access to your network greatly diminishes the risks of infection. In addition, using strong (not default or randomly generated) passwords also makes your network more secure, as the malware uses a basic list of guessable passwords.”





)