Cybersecurity Career Roadmap: Building Your Path in 2024

The Computer Emergency Response Team of Ukraine (CERT-UA) has warned that more than 2,000 computers in the country have been infected by a strain of malware called DirtyMoe.
The agency attributed the campaign to a threat actor it calls UAC-0027.
DirtyMoe, active since at least 2016, is capable of carrying out cryptojacking and distributed denial-of-service (DDoS) attacks. In March 2022, cybersecurity firm Avast revealed the malware’s ability to propagate in a worm-like fashion by taking advantage of known security flaws.
The DDoS botnet is known to be delivered by means of another malware referred to as Purple Fox or via bogus MSI installer packages for popular software such as Telegram. Purple Fox is also equipped with a rootkit that allows the threat actors to hide the malware on the machine and make it difficult to detect and remove.

The exact initial access vector used in the campaign targeting Ukraine is currently unknown. CERT-UA is recommending that organizations keep their systems up-to-date, enforce network segmentation, and monitor network traffic for any anomalous activity.
The disclosure comes as Securonix detailed an ongoing phishing campaign known as STEADY#URSA targeting Ukrainian military personnel with the goal of delivering a bespoke PowerShell backdoor dubbed SUBTLE-PAWS.
“The exploitation chain is relatively simple: it involves the target executing a malicious shortcut (.lnk) file which loads and executes a new PowerShell backdoor payload code (found inside another file contained within the same archive),” security researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov said.
The attack is said to be related to a threat actor known as Shuckworm, which is also known as Aqua Blizzard (formerly Actinium), Armageddon, Gamaredon, Iron Tilden, Primitive Bear, Trident Ursa, UNC530, and Winterflounder. Active since at least 2013, it’s assessed to be part of Russia’s Federal Security Service (FSB).
SUBTLE-PAWS, in addition to setting up persistence on the host, uses Telegram’s blogging platform called Telegraph to retrieve the command-and-control (C2) information, a technique previously identified as associated with the adversary since early 2023, and can propagate through removable attached drives.
Mexican financial institutions are under the radar of a new spear-phishing campaign that delivers a modified version of an open-source remote access trojan called AllaKore RAT.
The BlackBerry Research and Intelligence Team attributed the activity to an unknown Latin American-based financially motivated threat actor. The campaign has been active since at least 2021.
“Lures use Mexican Social Security Institute (IMSS) naming schemas and links to legitimate, benign documents during the installation process,” the Canadian company said in an analysis published earlier this week.

“The AllaKore RAT payload is heavily modified to allow the threat actors to send stolen banking credentials and unique authentication information back to a command-and-control (C2) server for the purposes of financial fraud.”
It seems that the attacks are specifically intended to target big businesses with annual sales of more than $100 million. Retail, agriculture, the public sector, manufacturing, transportation, commercial services, capital goods, and banking are among the industries targeted.
The first step in the infection chain is the distribution of a ZIP file through phishing or drive-by compromise. This file contains an MSI installer file that launches a.NET downloader, which verifies the victim’s geolocation in Mexico and retrieves the modified AllaKore RAT, a Delphi-based RAT that was first discovered in 2015.
“AllaKore RAT, although somewhat basic, has the potent capability to keylog, screen capture, upload/download files, and even take remote control of the victim’s machine,” BlackBerry stated.
The threat actor has added new features to the malware, such as support for banking fraud-related commands, targeting cryptocurrency trading platforms and banks in Mexico, initiating a reverse shell, extracting content from the clipboard, and fetching and executing additional payloads.

The campaign’s use of Mexico Starlink IPs and the addition of Spanish-language instructions to the modified RAT payload provide the threat actor with links to Latin America. Moreover, the lures used are only effective for businesses big enough to submit reports directly to the department of the Mexican Social Security Institute (IMSS).
“This threat actor has been persistently targeting Mexican entities for the purposes of financial gain,” the business stated. “This activity has continued for over two years, and shows no signs of stopping.”
The results coincide with the announcement from IOActive that it has discovered three vulnerabilities (CVE-2024-0175, CVE-2024-0176, and CVE-2024-0177) in the Lamassu Douro bitcoin ATMs that could provide physical access to an attacker the ability to take complete control of the machines and steal user data.
The ATM’s software update mechanism and its capacity to scan QR codes are exploited by the attackers to supply their own malicious file and start the execution of arbitrary code, thereby enabling the attacks. In October 2023, the Swiss company resolved the issues.
Google on Tuesday released updates to fix four security issues in its Chrome browser, including an actively exploited zero-day flaw.
The issue, tracked as CVE-2024-0519, concerns an out-of-bounds memory access in the V8 JavaScript and WebAssembly engine, which can be weaponized by threat actors to trigger a crash.

“By reading out-of-bounds memory, an attacker might be able to get secret values, such as memory addresses, which can be bypass protection mechanisms such as ASLR in order to improve the reliability and likelihood of exploiting a separate weakness to achieve code execution instead of just denial of service,” according to MITRE’s Common Weakness Enumeration (CWE).
Additional details about the nature of the attacks and the threat actors that may be exploiting it have been withheld in an attempt to prevent further exploitation. The issue was reported anonymously on January 11, 2024.
“Out-of-bounds memory access in V8 in Google Chrome prior to 120.0.6099.224 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page,” reads a description of the flaw on the NIST’s National Vulnerability Database (NVD).
The development marks the first actively exploited zero-day to be patched by Google in Chrome in 2024. Last year, the tech giant resolved a total of 8 such actively exploited zero-days in the browser.
Users are recommended to upgrade to Chrome version 120.0.6099.224/225 for Windows, 120.0.6099.234 for macOS, and 120.0.6099.224 for Linux to mitigate potential threats.
Users of Chromium-based browsers such as Microsoft Edge, Brave, Opera, and Vivaldi are also advised to apply the fixes as and when they become available.
The environmental services industry witnessed an “unprecedented surge” in HTTP-based distributed denial-of-service (DDoS) attacks, accounting for half of all its HTTP traffic.
This marks a 61,839% increase in DDoS attack traffic year-over-year, web infrastructure and security company Cloudflare said in its DDoS threat report for 2023 Q4 published last week.
“This surge in cyber attacks coincided with COP 28, which ran from November 30th to December 12th, 2023,” security researchers Omer Yoachimik and Jorge Pacheco said, describing it as a “disturbing trend in the cyber threat landscape.”
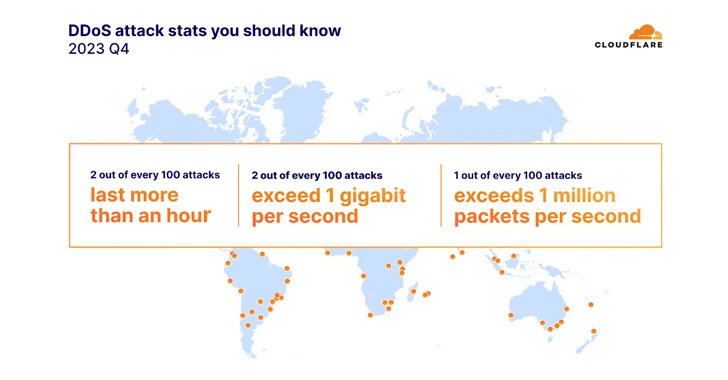
The uptick in HTTP attacks targeting environmental services websites is part of a larger trend observed annually over the past few years, specifically during COP 26 and COP 27, as well as other United Nations environment-related resolutions or announcements.
“This recurring pattern underscores the growing intersection between environmental issues and cyber security, a nexus that is increasingly becoming a focal point for attackers in the digital age,” the researchers said.
Despite the environmental services sector becoming a new target in Q4 2023, the cryptocurrency industry continues to be the primary casualty in terms of the volume of HTTP DDoS attack requests.
With more than 330 billion HTTP requests targeting it, the attack traffic represents more than 4% of all HTTP DDoS traffic for the quarter. Gaming and gambling and telecommunications emerged as the second and third most attacked industries.
On the other end of the spectrum are the U.S. and China, acting as the main sources of HTTP DDoS attack traffic. It’s worth noting that the U.S. has been the largest source of HTTP DDoS attacks for five consecutive quarters since Q4 2022.
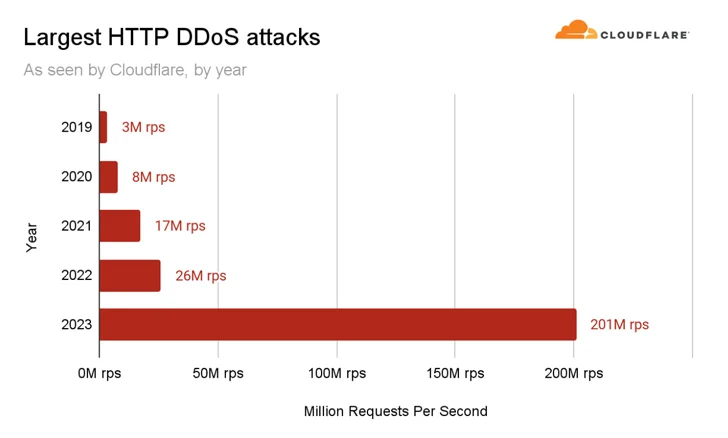
“Together, China and the U.S. account for a little over a quarter of all HTTP DDoS attack traffic in the world,” the researchers said. “Brazil, Germany, Indonesia, and Argentina account for the next 25%.”
The development comes amid a heavy onslaught of DDoS attacks targeting Palestinian banking, information technology (IT), and internet platforms following the onset of the Israel-Hamas War and Israel’s counteroffensive codenamed Operation Iron Swords.
The percentage of DDoS attack traffic targeting Palestinian websites grew by 1,126% quarter-over-quarter, Cloudflare said, adding DDoS attack traffic targeting Taiwan registered a 3,370% growth amidst the Taiwanese presidential elections and rising tensions with China.
Akamai, which also published its own retrospective on DDoS Trends in 2023, said “DDoS attacks became more frequent, longer, highly sophisticated (with multiple vectors), and focused on horizontal targets (attacking multiple IP destinations in the same attack event).”
The findings also follow a report from Cloudflare about the increasing threat posed by unmanaged or unsecured API endpoints, which could enable threat actors to exfiltrate potentially sensitive information.
“HTTP anomalies — the most frequent threat toward APIs — are common signals of malicious API requests,” the company said. “More than half (51.6%) of traffic errors from API origins comprised ‘429’ error codes: ‘Too Many Requests.'”
A 29-year-old Ukrainian national has been arrested in connection with running a “sophisticated cryptojacking scheme,” netting them over $2 million (€1.8 million) in illicit profits.
The person was apprehended in Mykolaiv, Ukraine, on January 9 by the National Police of Ukraine with support from Europol and an unnamed cloud service provider following “months of intensive collaboration.”
“A cloud provider approached Europol back in January 2023 with information regarding compromised cloud user accounts of theirs,” Europol said, adding it shared the intelligence with the Ukrainian authorities.
As part of the probe, three properties were searched to unearth evidence against the suspect.
Cryptojacking refers to a type of cyber crime that entails the unauthorized use of a person’s or organization’s computing resources to mine cryptocurrencies.
On the cloud, such attacks are typically carried out by infiltrating the infrastructure via compromised credentials obtained through other means and installing miners that use the infected host’s processing power to mine crypto without their knowledge or consent.
“If the credentials do not have the threat actors’ desired permissions, privilege escalation techniques are used to obtain additional permissions,” Microsoft noted in July 2023. “In some cases, threat actors hijack existing subscriptions to further obfuscate their operations.”
The core idea is to avoid paying for necessary infrastructure required to mine cryptocurrencies, either by taking advantage of free trials or compromising legitimate tenants to conduct cryptojacking attacks.
In October 2023, Palo Alto Networks Unit 42 detailed a cryptojacking campaign in which threat actors were found stealing Amazon Web Services (AWS) credentials from GitHub repositories within five minutes of their public disclosure to mine Monero.
Poorly secured Microsoft SQL (MS SQL) servers are being targeted in the U.S., European Union, and Latin American (LATAM) regions as part of an ongoing financially motivated campaign to gain initial access.
“The analyzed threat campaign appears to end in one of two ways, either the selling of ‘access’ to the compromised host, or the ultimate delivery of ransomware payloads,” Securonix researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov said in a technical report shared with The Hacker News.
The campaign, linked to actors of Turkish origin, has been codenamed RE#TURGENCE by the cybersecurity firm.
Initial access to the servers entails conducting brute-force attacks, followed by the use of xp_cmdshell configuration option to run shell commands on the compromised host. This activity mirrors that of a prior campaign dubbed DB#JAMMER that came to light in September 2023.
This stage paves the way for the retrieval of a PowerShell script from a remote server that’s responsible for fetching an obfuscated Cobalt Strike beacon payload.
The post-exploitation toolkit is then used to download the AnyDesk remote desktop application from a mounted network share for accessing the machine and downloading additional tools such as Mimikatz to harvest credentials and Advanced Port Scanner to carry out reconnaissance.
Lateral movement is accomplished by means of a legitimate system administration utility called PsExec, which can execute programs on remote Windows hosts.
That attack chain, ultimately, culminates with the deployment of Mimic ransomware, a variant of which was also used in the DB#JAMMER campaign.
“The indicators as well as malicious TTPs used in the two campaigns are completely different, so there is a very high chance these are two disparate campaigns,” Kolesnikov told
“More specifically, while the initial infiltration methods are similar, DB#JAMMER was slightly more sophisticated and used tunneling. RE#TURGENCE is more targeted and tends to use legitimate tools and remote monitoring and management, such as AnyDesk, in an attempt to blend in with normal activity.”
Securonix said it uncovered an operational security (OPSEC) blunder made by the threat actors that allowed it to monitor clipboard activity owing to the fact that the clipboard sharing feature of AnyDesk was enabled.
This made it possible to glean their Turkish origins and their online alias atseverse, which also corresponds to a profile on Steam and a Turkish hacking forum called SpyHack.
“Always refrain from exposing critical servers directly to the internet,” the researchers cautioned. “With the case of RE#TURGENCE attackers were directly able to brute force their way into the server from outside the main network.”
Thanks to technological advancements, we can find any information on Google. We can use Google search engine to seek any data, resources, and information. No wonder Google has made our lives so easier and hassle-free.
However, there is still a lot of data on Google that we don’t know about. Using a hacking technique called Google Dorking, we can find hidden information within minutes. Many hackers use it to hack into sensitive data and collect crucial information. Hence, it is important for ethical hackers to understand what is Google Dorking and gain a fair understanding to prevent such attacks.
In this blog post, we will learn about the Google hacker database, Google Dorking commands, and more in detail.
Google Dorking, or Google Hacking, means using Google search-hacking techniques to hack into sensitive information and sites that are not available in public search results.
Google Dorking involves using advanced search operators and specific keywords to narrow down search results and discover potentially vulnerable websites, exposed data, or other valuable information.
For example, users can click on various tags, such as sites or images, to extract information or images from a website. They can also use a Google Dork cheat sheet containing different commands to get specific search results.
The Google Dorking technique is often used by security professionals, hackers, and researchers to uncover sensitive or hidden information on the internet.
Some common examples of Google Dorking queries include:
You can search for specific file types, such as PDFs, spreadsheets, or databases, using queries like “filetype:pdf” or “filetype:xls.”
Queries like “inurl:login” or “intitle:login” can help you find websites with login pages that may be vulnerable to security exploits.
Searches like “intitle:webcamxp inurl:8080” can reveal webcams or other devices with known vulnerabilities.
Queries like “intitle:index.of” can help you find open directories on web servers that may contain sensitive information.
You can use queries to search within a specific website, like “site:example.com keyword” to find information on a particular domain.
Google Dorking can be used for various purposes, both legitimate and potentially malicious, depending on the intent of the user.
Here are some common uses of Google Dorking:
Security professionals and researchers use Google Dorking to gather information about websites, servers, and online assets. This can help identify vulnerabilities, assess the security of web applications, and uncover potential threats.
Security experts may use Google Dorking to identify websites or systems that have known vulnerabilities. This information can be used to alert website owners or organizations to security issues that need to be addressed.
Companies may use Google Dorking to gain insights into the online presence and strategies of their competitors. This can involve finding hidden web pages, identifying keywords, or uncovering marketing tactics.
Researchers and academics may use Google Dorking to discover information for their studies and investigations. It can be a valuable tool for finding publicly accessible data and resources.
Website administrators and owners can use Google Dorking to check the indexability of their site’s content, monitor search engine rankings, and assess the visibility of their web pages.
Content creators and bloggers may use Google Dorking to find specific types of content, such as PDFs, images, or research papers, that are relevant to their work.
Ethical hackers and penetration testers use Google Dorking to identify potential entry points and vulnerabilities in systems and websites as part of security assessments. This helps organizations strengthen their security measures.
Individuals concerned about their online privacy may use Google Dorking to see what personal information or data is publicly accessible through search engines and take steps to protect their online presence.
A Google Dorking cheatsheet is a quick reference guide that provides a list of commonly used Google Dorking commands and operators. Here’s a Google Dork cheat sheet for your reference:
| Purpose | Google Dorking Command |
| Find Microsoft Word documents | filetype:doc |
| Find text documents | filetype:txt |
| Find PowerPoint presentations | filetype:ppt |
| Find PDF files | filetype:pdf |
| Find Excel spreadsheets | filetype:xls |
| Find open directories on web servers | intitle:”Index of /” |
| Find Apache default pages | intitle:”Apache2 Debian Default Page” |
| Find Nginx default pages | intitle:”Welcome to nginx!” |
| Find open IIS servers | intitle:”Welcome to IIS” |
| Search for login pages | intitle:”Login” or intitle:”Log In” |
| Search for directory listings | intitle:”Index of /” or intitle:”Browse Directory” |
| Find exposed configuration files | intitle:”config.json” |
| Identify exposed Git repositories | intitle:”index of” inurl:.git |
| Find vulnerable Apache Tomcat installations | intitle:”Apache Tomcat” intitle:”Administration” |
| Discover open Jenkins instances | intitle:”Dashboard [Jenkins]” |
| Search for exposed Subversion repositories | intitle:”Index of /svn” |
| Find open phpMyAdmin installations | intitle:”phpMyAdmin” or intext:”phpMyAdmin MySQL-Dump” |
| Locate exposed Microsoft SharePoint documents | intitle:”Microsoft SharePoint” intext:”Sign in to SharePoint” |
| Find exposed Redis servers | intitle:”Redis” intext:”Server Information” |
| Search for open Elasticsearch instances | intitle:”Elasticsearch Head” |
| Discover exposed MongoDB databases | intitle:”MongoDB Server Information” |
| Identify open CouchDB instances | intitle:”CouchDB – Welcome” |
| Search for exposed Memcached servers | intitle:”Memcached Server Information” |
| Find open RDP servers | intitle:”remote desktop inurl:rdweb” |
| Locate exposed VNC servers | intitle:”VNC viewer for Java” |
| Find open Telnet servers | intitle:”welcome to” intext:”telnet” |
| Search for exposed SNMP devices | intitle:”welcome to” intext:”snmp” |
| Find open SMB shares | intitle:”Index of /smb.conf” |
| Identify open FTP servers | intitle:”Index of /ftp” |
| Search for open NFS shares | intitle:”Index of /exports” |
| Find open network printers | intext:”printer meter” |
| Search for open VoIP systems | intitle:”Asterisk Management Portal” |
| Identify exposed AXIS cameras | intitle:”Live View / – AXIS” |
| Discover unsecured webcams | intitle:”webcamXP 5″ inurl:8080 |
| Find open Linksys webcams | intitle:”Linksys Viewer – Login” -inurl:mainFrame |
| Search for exposed D-Link webcams | intitle:”D-Link” inurl:”/video.htm” |
| Find open Panasonic IP cameras | intitle:”Panasonic Network Camera” |
| Locate open Foscam cameras | intitle:”Foscam” intext:”user login” |
| Identify open Samsung Smart TVs | intext:”SMART TV” inurl:password.txt |
| Search for open Netgear routers | intitle:”Netgear” intext:”NETGEAR” |
| Discover open Ubiquiti devices | intext:”Ubiquiti” intitle:”AirOS” |
| Search for open MikroTik routers | intext:”MikroTik RouterOS” inurl:winbox |
| Find exposed Siemens SCADA systems | intitle:”Siemens SIMATIC” intext:”Web Server” -inurl:/portal |
| Locate open Schneider Electric systems | intext:”Schneider Electric” intitle:”PowerLogic Web- |
| Search for exposed Johnson Controls systems | intitle:”Johnson Controls – WorkPlace” intext:”User name :” |
Along with several Google Dork commands and operators, there are some advanced combinations of operators too that you can use to filter search results to maximize efficiency.
However, you can refer to the Google Hacker database to avoid typing these operators and combinations every time to search for any information. This database contains hundreds of combinations of multiple and advanced operators.
Find webcams with known vulnerabilities:
intitle:"D-Link" inurl:"/view.htm"
Search for Elasticsearch instances containing specific data:
intext:"kibana" intitle:"Kibana"
Search for MongoDB instances without authentication:
intext:"MongoDB Server Information" intitle:"MongoDB" -intext:"MongoDB Server Version"
Search for OpenCV instances with exposed data:
intitle:"OpenCV Server" inurl:"/cgi-bin/guestimage.html"
Search for InfluxDB instances with default configurations:
intitle:"InfluxDB - Admin Interface"
Search for RabbitMQ management interfaces:
intitle:"RabbitMQ Management"
Search for Jenkins builds with specific information:
intitle:"Console Output" intext:"Finished: SUCCESS"
Search for Grafana dashboards:
intitle:"Grafana" inurl:"/dashboard/db"
Search for NVIDIA Jetson devices with open ports:
intitle:"NVIDIA Jetson" intext:"NVIDIA Jetson"
Search for Fortinet devices with open interfaces:
intext:"FortiGate Console" intitle:"Dashboard"
Search for OpenEMR installations with specific data:
intitle:"OpenEMR Login" inurl:"/interface"
Search for Jenkins script consoles with default credentials:
intitle:"Jenkins Script Console" intext:"Run groovy script"
These advanced commands for Google dorking can be useful for specific security assessments and research purposes. Always ensure you have proper authorization and follow ethical guidelines when using advanced Google Dorking commands. Unauthorized or malicious use can have serious legal and ethical consequences.
Google Dorking tools are software or scripts designed to automate the process of searching for specific information using Google Dorking queries. These tools can help security professionals, researchers, and ethical hackers efficiently discover vulnerabilities and sensitive information on the internet.
Here are a few Google Dorking tools and resources:
The GHDB is a collection of Google Dorking queries and examples created and maintained by the security community. It serves as a reference for finding information on the internet, including vulnerabilities and exposed data. You can access it at https://www.exploit-db.com/google-hacking-database.
There are various open-source and commercial tools available that facilitate Google Dorking. These tools often provide a user-friendly interface for constructing and executing Dorking queries. Examples include “DorkMe” and “Google Hacking Database Scraper.”
While not specifically a Google Dorking tool, Shodan is a search engine that focuses on finding internet-connected devices and services. It can be used to discover open ports, exposed services, and vulnerable devices. Shodan provides its own set of search operators to find specific information.
Some security professionals and researchers develop custom scripts or automation tools to conduct Google Dorking searches tailored to their specific needs. These scripts can help streamline the process of searching for vulnerabilities and exposed data.
Some web vulnerability scanners incorporate Google Dorking functionality as part of their scanning process. These scanners can automatically use Dorking queries to identify potential security issues on websites and web applications.
Many penetration testing frameworks, such as Metasploit and Burp Suite, include modules or extensions that allow security professionals to integrate Google Dorking into their assessments.
On Monday, representatives from Taiwan, the US, and India started a two-day discussion aimed at exchanging best practices and strengthening operational knowledge on cybersecurity-related matters.

Here, at a joint workshop called by the Global Cooperation and Training Framework (GCTF), discussions took place.
This event was co-hosted by the United Service Institution of India, Taiwan’s Representative to India, Baushuan Ger, and former national cybersecurity coordinator of India, Lt Gen Rajesh Pant, according to a press statement from the US embassy. It was the country’s first-ever in-person GCTF program.
A memorandum of understanding was signed by Taiwan and the US to create the GCTF, a forum for using Taiwan’s capabilities and knowledge to tackle worldwide issues that both countries find important.
“To improve cybersecurity and safeguard our common interests in the digital sphere, the US is dedicated to collaborating closely with partners like Taiwan and India,” stated Garcetti. Instead of worrying about how technology can be used to oppress or divide us, he stated, “we can fully utilize the almost infinite potential that these advancements will bring when we connect, protect, and detect with it.”
Taiwan’s Ambassador to India, Ger, emphasized the value of the GCTF as a forum for using Taiwan’s advantages and know-how to tackle worldwide concerns.
According to Lt Gen Pant, cybersecurity plays a significant role in national security for India, which has 1.2 billion smartphones and over 800 million internet users.According to Lt Gen Pant, cybersecurity plays a significant role in national security for India, which has 1.2 billion smartphones and over 800 million internet users.
With involvement from more than 120 nations, the GCTF has organized 70 international workshops since its founding in 2015 with the goal of fostering relationships between specialists in fields including digital health, supply chains, public health, humanitarian aid, and other regional concerns. The GCTF, which provides Taiwan with a forum to share its knowledge with partners worldwide, is jointly administered by the US, Taiwan, the Australian Office, Taipei, and the Japan-Taiwan Exchange Association.

Windows KMS Activator is a widely discussed tool in the realm of software activation. It’s a popular solution for individuals and organizations looking to activate Microsoft Windows and Microsoft Office products. While this tool can be a practical solution for users seeking to avoid expensive licensing fees, it’s essential to understand how it works and its legal implications. In this article, we’ll delve into the world of Windows KMS Activator, discussing its functionality, potential risks, and the best practices for its usage.
KMS, or Key Management Service, is a technology developed by Microsoft to activate volume-licensed versions of their software products. It’s mainly used by organizations that have numerous Windows or Office installations and want to manage them efficiently without entering individual product keys for each installation. KMS allows these organizations to activate their software centrally through a server.
Windows KMS Activator, also known as Windows Key Management Service Activator, is a third-party tool that emulates the functionality of Microsoft’s KMS service. This tool is primarily used to activate Windows and Office products, simulating a KMS server, without requiring a legitimate product key. It’s typically used by individuals or organizations who want to use Microsoft software without purchasing licenses.
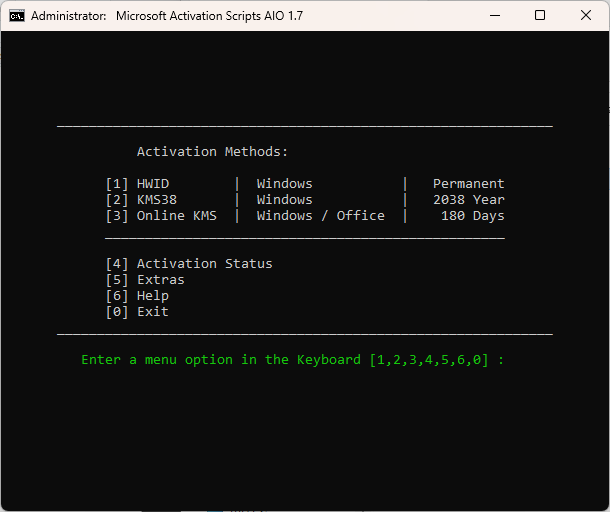
It’s crucial to understand that using Windows KMS Activator or similar tools falls into a legal gray area. Microsoft’s licensing terms explicitly state that using unauthorized activation methods, including KMS emulators, is against their terms of service. If you or your organization is caught using KMS activators in violation of licensing agreements, there can be legal consequences, including fines or other penalties.
Moreover, relying on KMS activators means you’re not receiving official updates or support from Microsoft, which could lead to security and compatibility issues. It’s always advisable to adhere to legal and ethical standards by acquiring legitimate licenses for Microsoft products.
Using Windows KMS Activator poses several potential risks:
Click on the given button and run as admin
If you are still considering using a KMS activator, you should do so with caution:

Windows KMS Activator and similar tools might seem like a convenient way to activate Microsoft products without purchasing licenses, but they come with significant legal, security, and ethical risks. It’s always advisable to obtain legitimate licenses for Microsoft software, ensuring both legal compliance and the best user experience. While KMS activators might offer short-term benefits, the long-term costs and risks often outweigh the savings.
Also Read- How To Get A Sponsor For Youtube Channel